Document fraud detection has become one of the hardest problems for underwriting, risk, operations, and compliance teams to combat. Not because teams are not diligent, but because fraud no longer looks suspicious.
Many fraudulent documents today are clean, internally consistent, and professionally generated. They pass manual document review because they are designed to do exactly that. The tools used by those wishing to manipulate application documents have evolved significantly, even over the last few years, let alone the last decade.
This guide explains what document fraud really looks like today, which documents are most commonly faked, why manual document review fails, and what effective document fraud detection needs to focus on.
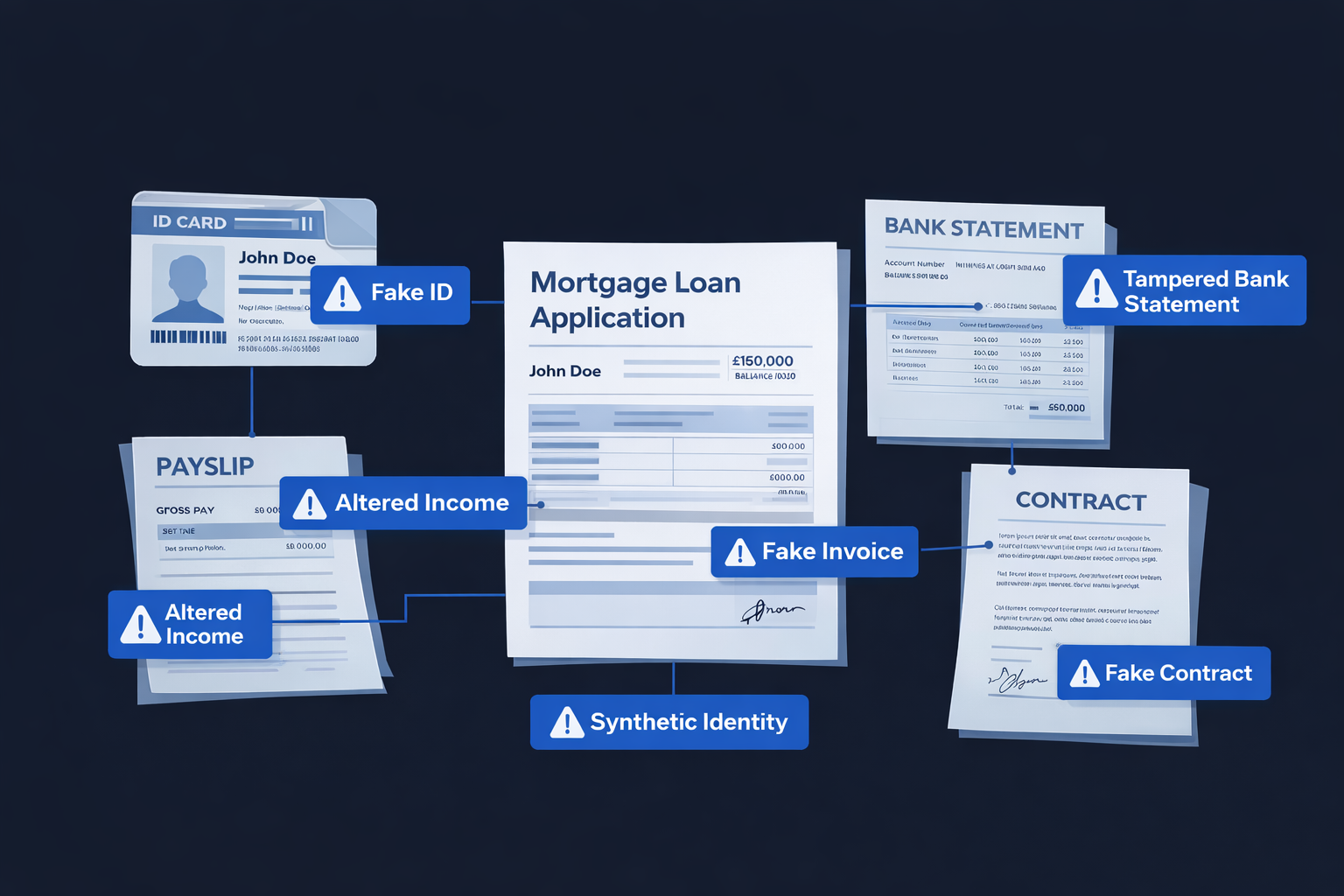
What Is Document Fraud?
Document fraud occurs when documents are used to misrepresent reality. We see this across many industries. It is common for people to change invoice information during an insurance claims process, manipulate their address to create multiple accounts on a gambling website, inflate their salary to gain access to better mortgage rates, or delete transactions to alternative business lenders when applying for a commercial finance loan, and so on.
Document fraud can include:
Fully fabricated documents
Genuine documents that have been altered
Multiple documents that are individually believable but collectively false
Broadly, in financial decision-making, fraudulent documents are often used to:
Inflate income or revenue
Hide liabilities or financial instability
Misrepresent business ownership or control
Strengthen applications just enough to pass approval thresholds
Expose weaknesses in the defence systems of organisations, allowing fraud rings to operate
The most damaging document fraud is not obvious. It is compliant-looking and process-aware. When a junior compliance executive is forced to decide whether Calibri_Light or Calibri-Light is the correct font for a challenger bank they have rarely encountered before, decisions become problematic very quickly.
Modern document analysis tools like Fraudfinder use matching and learning algorithms that store layout, formatting, and structural information from every document processed. These systems evolve continuously and can validate changes in seconds.
Why Manual Document Review Is No Longer Enough
Manual document review was built for a different era of fraud.
Historically, fake documents were easier to spot. Inexperienced fraudsters often left obvious signs of manipulation such as poor formatting, visible edits, mismatched totals, or inconsistent fonts. This was popularised in film when Leonardo DiCaprio portrayed the real-life fraudster Frank Abagnale in Catch Me If You Can, travelling the world fooling bank employees with visibly altered documents. Detection relied on spotting clear visual mistakes.
Compliance analysts were trained to look for these surface-level indicators. Today, those signals rarely exist.
While some compliance and fraud professionals are trained to analyse PDF metadata, this becomes far more difficult when:
Banks frequently change their PDF structures and templates
Statements and documents are accepted as scanned images as well as PDFs
New banks and financial institutions appear regularly
Analysts have no access to a meaningful dataset to benchmark metadata characteristics
Modern fraud, by contrast, is engineered around the rules of manual review.
Manual checks typically ask: “Does this document look real?”
Modern fraud answers “yes”, while still being false.
A document can be visually authentic, internally consistent, and professionally produced while still misrepresenting the truth.
With the rise of AI models, improved SaaS tools, and more accessible technology, sophisticated fraudsters can easily mimic document templates while subtly manipulating the data to appear genuine. For this reason, modern document fraud analysis tools like Fraudfinder must use a combination of machine learning, external data validation, and custom-built fraud checks to provide meaningful protection against this growing threat.
Common Types of Document Fraud
Document Alteration
Small but intentional edits to real documents:
Adjusted income or revenue
Shifted dates
Changed names or account details

These changes are subtle and rarely visible during fast reviews. See an example with Millbrook Finance here, where the dates and balance data were manipulated on an applicant bank statement to secure a business loan of over £50,000.
This type of fraud must not be treated lightly. Just because it is easy to open a computer and alter a date in a document does not mean the impact is minimal. If the forgery successfully fools a compliance or risk team, no matter how minor it appears, it can lead to considerable financial loss further down the line.
Fabricated Documents
Entire documents created from scratch, including:
Contracts
Letters
Financial summaries
Certificates
AI and modern document tools can and do make these documents clean and convincing. See an example below where Fraudfinder identified a fabricated Council Tax bill that was a key piece of evidence for a bridging loan valued at £800,000.
The applicant had deleted key information showing they were in arrears on their council tax payments. The information in blue represents data deleted.
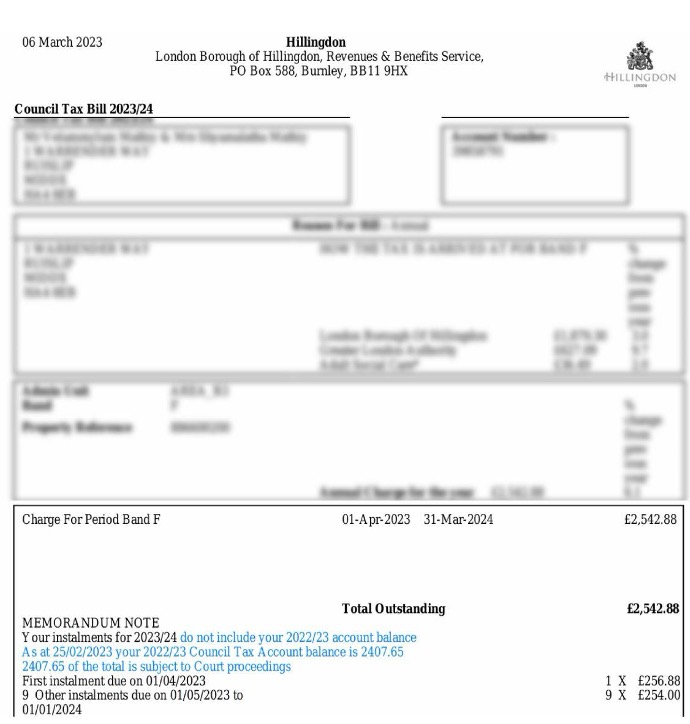
No human reviewer could identify this type of forgery because the incriminating information had been removed entirely. Only through technology can deleted data be restored, allowing organisations to see the full truth that the original document would have conveyed.
Image and Layout Manipulation
Fraudsters modify:
Logos
Tables and columns
Signatures and stamps
Scanned pages
The document looks authentic, while the data inside has changed.
We see issues with signatures and stamps frequently. A common tactic in the mortgage and conveyancing space involves small solicitor firms certifying copies of bank statements or financial documents as originals. These documents are printed, stamped as certified copies, and scanned back into the application process.
Why does this cause problems?
It is unlikely that the solicitors involved have access to the technology required to validate whether bank statements are truly original, meaning in the original format and structure issued by the bank.
This allows sophisticated fraudsters, who have ensured there are no mathematical errors and have perfectly mimicked a bank’s template, to bypass manual review processes. The credibility lent by a certified copy stamp often completes the deception, convincing lender fraud and risk teams that the document is genuine.
Scanned and image-based documents also contain far less metadata than original PDFs, leaving fewer elements to analyse. While tools like Fraudfinder can assess scans effectively, PDFs remain the gold standard for document collection and analysis. This is one reason banks issue documents in PDF format.
Each conversion, from PDF to print to scan, removes layers of validation. Scans do not contain font data, scanning software alters producer information, and visual clarity can degrade. Each step increases the chance of review error.
First-Party Fraud
Real individuals or businesses altering their own documents to appear stronger:
Inflated income
Smoothed cash flow
Extended trading history
This is one of the most common forms of financial document fraud. CIFAS reported that in a study conducted last year, 16 per cent of mortgage applicants admitted to committing first-party fraud to secure a mortgage. It is common because it is easy and carries a low perceived risk from the applicant’s perspective.
Synthetic Profiles
A mix of real and fake information across multiple documents. Each document passes individually, but together they do not.
This is not a new tactic. Many financial providers request six months of bank statements, payslips, and identification to cross-check data consistency. However, fraudsters may submit legitimate documents for several months and introduce a fabricated document for a specific period that goes unnoticed.
It is often within that single altered document that signs of money laundering or broader financial crime exist.
Financial Documents Most Commonly Faked
Financial Statements
Often edited to inflate revenue or remove liabilities. Fraud commonly appears as numbers that are unnaturally smooth or stable. In business finance and bridging markets, we frequently see transactions to other lenders removed to make businesses appear less leveraged than they truly are.
Bank Statements
Bank statement fraud is one of the most common forms of document manipulation we encounter. Bank statements tell a comprehensive financial story, including income, affordability, spending patterns, address history, employer details, and cash flow.
Common forms of bank statement fraud include:
Edited PDFs
Reconstructed layouts
Altered transaction histories
Metadata inconsistencies
Manipulated addresses
These issues are difficult to detect manually. Effective detection relies on large and continually evolving datasets. Fraudfinder analyses layout and metadata characteristics from thousands of files daily, identifying authenticity patterns and flagging deviations that warrant concern.
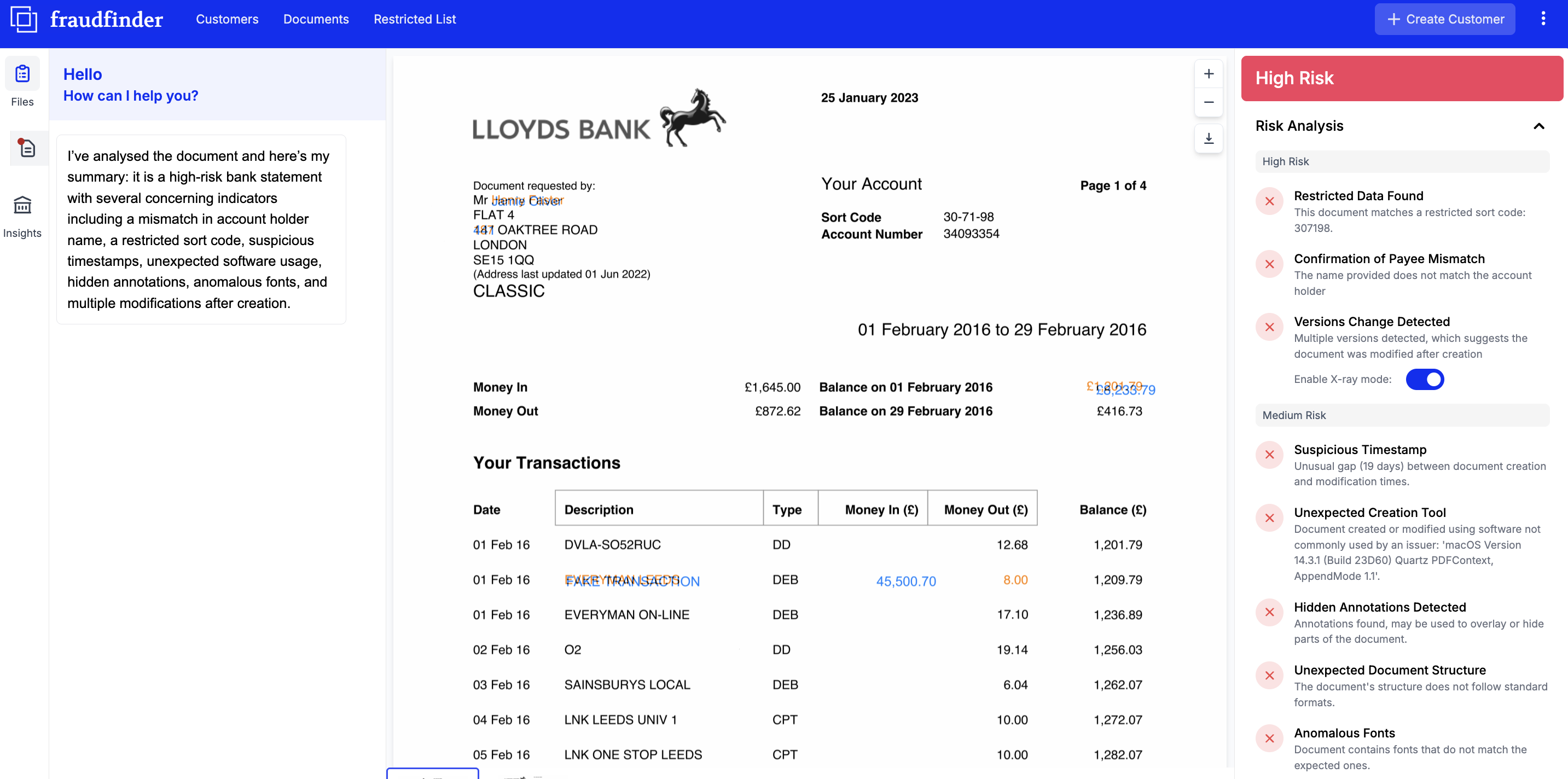
Below, we see an example of a fake bank statement that has a series of metadata issues. We can see restricted data; the name/address on the statement does not match the account details; there has been manipualted data in the address and transactions; the timestamp, software; fonts and document structure are all incorrect for this document issuer, Lloyds Bank.
Contracts
Used to suggest partnerships or obligations that do not exist and are often trusted without adequate verification.
Identity Documents
Used to hide true ownership or decision-makers, increasing regulatory and credit risk. Identity verification has improved significantly through tools like live image capture and biometric checks.
However, these processes are not without risk. Advances in AI-generated deepfakes mean even video-based verification can be compromised when fraudsters use sufficiently sophisticated tools.

Addresses and Location Data
Fake or borrowed addresses are used to appear more established or lower risk.
Proof of address can be validated in several ways, and most robust systems rely on automation rather than manual review. Fraudfinder can detect address manipulation by analysing font consistency, identifying restored or altered data, and extracting information from embedded barcodes where present.
Additional validation techniques include:
Electoral roll and residency checks
Google Maps address validation
Physical address verification through card delivery
Tax Documents
Edited or fabricated to inflate income or support synthetic profiles. This is increasingly common as economic pressure increases reliance on borrowing among self-employed individuals and sole traders. Documents like SA302s are standardised and therefore particularly vulnerable to templated manipulation.
Why Fraudulent Documents Pass Manual Review
Document fraud succeeds because of structural blind spots.
Documents Are Reviewed in Isolation
Patterns emerge at scale. Organisations like Fraudfinder benefit from access to millions of documents, allowing validity patterns to be identified.
Legitimate-Looking Output Is Trusted
Professional generation is mistaken for truthful data.
Statistical Improbability Is Hard to Spot Manually
Fraudulent data often appears unnaturally clean.
Metadata and Timing Are Ignored
Creation and edit history often reveal more than visuals. Fraudsters are increasingly learning to mimic metadata as well.
Cross-Document Contradictions Go Unseen
Fraud often breaks across documents, not just within a single one.
What Effective Document Fraud Detection Looks Like
Modern document fraud detection focuses on:
Structural and layout consistency
Metadata and file-level signals
Statistical patterns across large volumes
Cross-document comparison
Behavioural and historical signals
External data validation techniques
These are data problems, not judgment problems, and they require scale, automation, and external context to solve.
Why Document Fraud Detection Matters
Prevents Financial Loss
Fraudulent documents lead to approvals that should never occur, exposing both applicants and financial institutions to significant risk.
Improves Risk Decisions
Accurate documents produce accurate decisions. Inaccurate inputs allow fraud rings to exploit weaknesses.
Supports Compliance
Fake documents undermine KYB and AML obligations. Regulatory bodies such as the FCA impose severe penalties for inadequate controls.
Improves Operational Efficiency
Automation reduces manual workload while increasing accuracy. AI and automation are not optional enhancements. They are permanent fixtures of modern risk operations
Document fraud today is as much about simulation as it is about deception.
Modern fraudsters no longer try to fool people. They try to satisfy processes. They understand what manual reviewers look for and ensure those boxes are ticked while hiding manipulation elsewhere.
If your document checks rely on what looks right, you are already exposed. Effective document fraud detection shows you what manual review cannot.



